Runtime Protection (RASP)
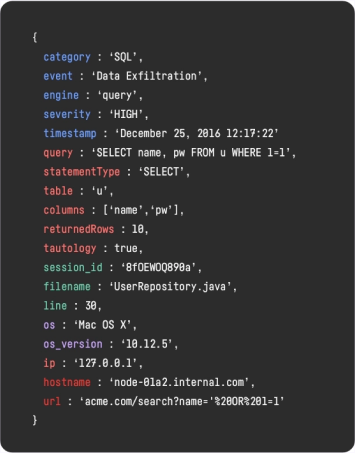
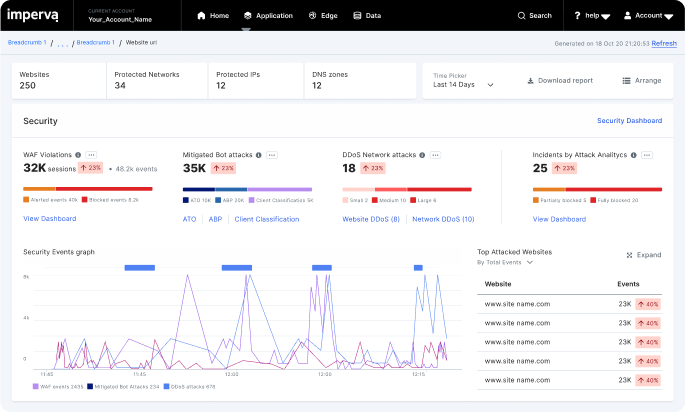
Imperva RASP uses Language Theoretic Security (LANGSEC) to detect and neutralize known and zero-day attacks, ensuring applications are secure by default. With Imperva RASP, businesses can identify vulnerabilities, patch them on their schedule, and maintain optimal performance. Secure your applications now with Imperva RASP.